Ransom Warrior Victims can now retrieve files for free
Researchers at Check Point have figured out the encryption method used by RansomWarrior. The Ransomware was developed in India.
The ransomware has targeted Windows users, the payload is delivered as an executable under file name “A Big Present.exe” if the application is executed it will encrypt files with a .THBEC extension. The victims are given a link to the dark web website that takes payments in Bitcoin.
The Ransomware offers the victims to decrypt two files for free, however if the victims don’t pay the ransom they will not get the rest of their files back. The ransomware cheekily has a sentence saying that the police can’t help you.
How Did The Researchers Break the Encryption?
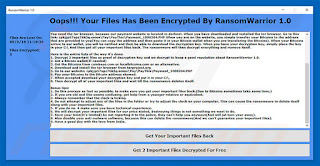 |
| source img:https://www.pcrisk.com |
Researchers at Check Point found the malware was developed by some inexperienced hackers, the company was able to retrieve decryption keys from the malware. Check Point succeeded due to the weak encryption used by the ransomware. The Ransomware used only 1000 hard-coded keys within the RansomWarrior binary code.
The Key’s index is saved in the victim’s machine which is providing the means to unlock the files. The Researchers were able to create a decryption tool to retrieve the files of any user who might have been affected by the Ransom Warrior. Most of the ransomware authors have been deploying mass spam messages to affect the entire networks.
Why Ransomware Became famous?
Some Ransomware products have made over $6 Million by just following a targeted campaign. However many have seen a move away from ransomware with a new focus on Cryptocurrency mining.
Source:https://latesthackingnews.com/2018/09/02/ransomwarrior-victims-can-now-retrieve-files-for-free


Comments
Post a Comment